Throughout SarCraft’s tumultuous history, players have discovered and weaponized numerous exploits that have fundamentally shaped the server’s politics, wars, and evolution. These loopholes in Minecraft’s mechanics and SarCraft’s custom systems have often proved more powerful than any enchanted weapon or tactical brilliance.
Illegal Items
Fishie’s boobs
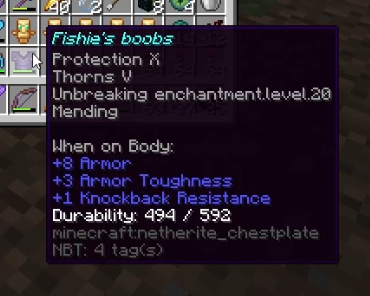
WhoIsFishie’s boobs is a hacked chestplate with powerful enchants that has become legendary among server veterans. The origins of this illegitimate armor remain shrouded in mystery - it’s unknown when or how it was spawned into the world, though many suspect it originated during one of shihaam_me’s power trips.
The armor features Protection X, Thorns V, Unbreaking XX, and Mending I - enchantment levels far beyond vanilla Minecraft’s limitations.
Hacked leggings
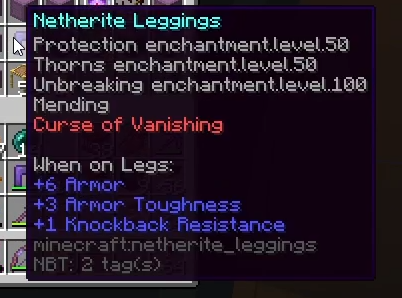
This item was secretly possessed by the Chicken Factory faction, with its existence kept carefully hidden from the broader server population. Unlike Fishie’s Boobs, these leggings were never used in combat as the thorns enchantment would have been a dead giveaway of their illegitimate nature. They remained a closely guarded secret - a nuclear option the faction kept in reserve but never deployed.
Cockstone
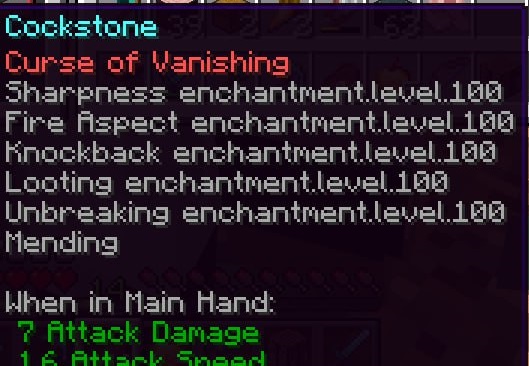
a illegal sword spawned in during the Telegram Command Injection exploit
Name: Cockstone Enchantments:
- Fire Aspect: 100
- Knockback: 100
- Looting: 100
- Mending: 1
- Sharpness: 100
- Unbreaking: 100
- Vanishing Curse: 1
Perhaps would get banned for being the recipient of this item
the item would later be renamed to a classified name
Stonecock
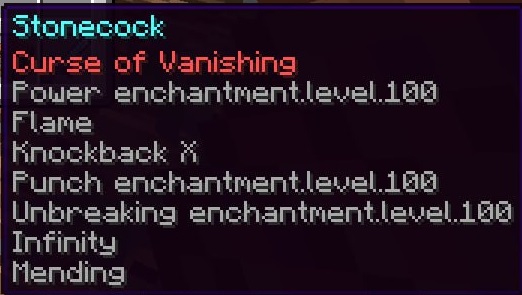
a illegal bow spawned in by WhoIsFishie during the Telegram Command Injection exploit
the bow would later be renamed to AIM_BOT to prevent the item being resurfaced
Hacked Chestplate
a ChestPlate spawned in by WhoIsFishie during the Telegram Command Injection exploit
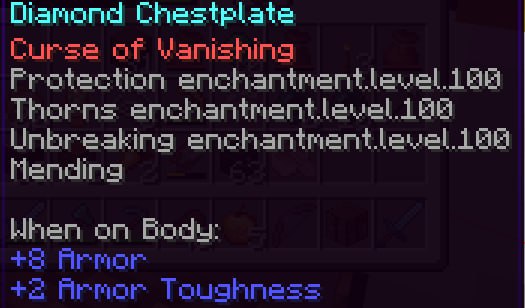
the item would later be renamed to Bra
Hacked Helmet
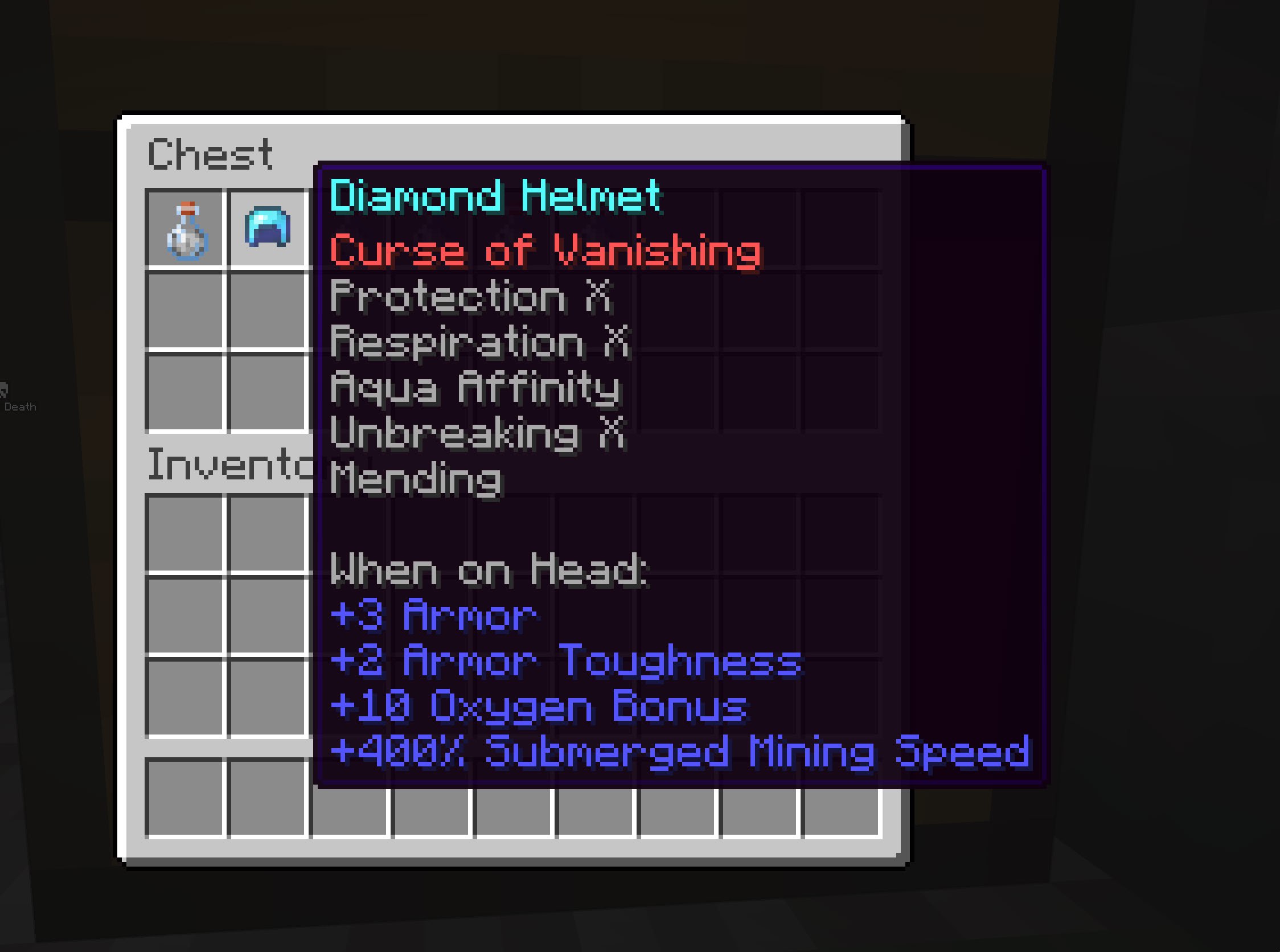
an illegal helmet admins found located in a structure Anoojfunaid was near
Exploits
Chunk Dupe of Season 2
a method of overloading a chunk to save its state would allow players to duplicate all items in a chunk. its unknown if Nazi’s used this or not.
Donkey Dupe of Season 3
Perhaps the most influential duplication glitch in server history, this two-person exploit allowed for unlimited item duplication by exploiting the server’s item handling.
The method required one player to ride a donkey and log off while another player kept the donkey’s inventory open. This timing mismatch in data saving created a window where items could be infinitely duplicated - explaining the Nazi faction’s peculiar fixation on horse breeding during this season.
This exploit fueled the infamous “Expensive Donkey Incident,” where Anoojfunaid accidentally fed an Enchanted Golden Apple to the very donkey they were using for duplication.
Shulker Dupe of Season 5
A duplication exploit used by player WhoIsFishie, who created a custom mod disguised as a shulker box sorting utility. The mod was cleverly designed to avoid detection by appearing as a legitimate quality-of-life modification. When opening a shulker box, the mod would present two seemingly innocent sorting buttons that actually enabled:
- Duplication of the first item in the box
- Duplication of the entire shulker box contents
The mod was distributed privately among a select group of players and remained undetected by administration due to its deceptive nature.
REDACTED Dupe of Season 10
read more at 3.1 REDACTED INFO EXPLOIT
Authentication Exploits
Sarcraft’s most devastating and long-lived exploits stemmed from the Telegram-based authentication plugin created by Udit. What began as a security measure became the source of the server’s most notorious vulnerabilities.
Telegram Command Injection
Perhaps the most insidious exploit discovered in the Minegram system was a command injection vulnerability that allowed players to execute arbitrary server commands through specially crafted Telegram messages. The exploit worked by exploiting how the plugin parsed and processed messages from Telegram to Minecraft.
To execute the exploit, a player would:
- Send a message in this specific format to break out of the tellraw JSON structure:
uh","color":"white"}]
say hello tellraw @p
["",{"text\":"hhh
- When replied to, this malformed message would cause the plugin to incorrectly parse the command structure, allowing the attacker to inject arbitrary commands that would be executed with server permissions.
This vulnerability effectively granted remote code execution through Telegram, allowing players to run any server command without authentication or logging in. The exploit remained undiscovered by administrators for an extended period, as the commands appeared to come from the server itself rather than from a specific player. while this exploit existed the since Season 5 it would be discovered in Season 10
Technical Deep Dive: The Injection Point
The vulnerability resided in the TgToMc module of the Minegram codebase, specifically in how it handled message replies. Examining the actual code reveals the exact injection point:
// TgToMc module
// Sends messages from Telegram
// to Minecraft with support
// for replies.
func TgToMc(data utils.ModuleData) {
(*data.TeleBot).Handle(tb.OnText, func(m *tb.Message) {
if len(*data.OnlinePlayers) > 0 {
sender := strings.ReplaceAll(m.Sender.FirstName+" "+m.Sender.LastName, "\n", "(nl)")
content := strings.ReplaceAll(m.Text, "\n", "(nl)")
if m.IsReply() {
if m.ReplyTo.Text == "" {
m.ReplyTo.Text = "[unsupported]"
}
m.ReplyTo.Text = strings.ReplaceAll(m.ReplyTo.Text, "\n", "(nl)")
_, err = io.WriteString(*data.Stdin, "tellraw @a [\"\",{\"text\":\"[TG] "+sender+"\",\"color\":\"aqua\"},{\"text\":\": \"},{\"text\":\"(\",\"color\":\"yellow\"},{\"text\":\"reply\",\"bold\":true,\"color\":\"yellow\",\"hoverEvent\":{\"action\":\"show_text\",\"contents\":\""+m.ReplyTo.Text+"\"}},{\"text\":\")\",\"color\":\"yellow\"},{\"text\":\" "+content+"\"}]\n")
} else {
_, err = io.WriteString(*data.Stdin, "tellraw @a [\"\",{\"text\":\"[TG] "+sender+"\",\"color\":\"aqua\"},{\"text\":\": "+content+"\",\"color\":\"white\"}]\n")
}
}
})
The critical vulnerability is in how the code directly injects m.ReplyTo.Text (the content of the message being replied to) into the JSON structure of the tellraw command without proper escaping or sanitization. When a player crafted a message containing JSON closing syntax like "}] followed by a new command, the tellraw JSON structure would prematurely terminate.
The attack works because:
- The malicious message is stored in Telegram and retrieved as
m.ReplyTo.Textwhen someone replies to it - While the code does replace newlines with “(nl)”, it fails to escape or validate JSON special characters
- The string
"}]closes the JSON array prematurely - Any text that follows, like
say hello, becomes a new command executed by the server - The final portion
tellraw @p ["",{"text\":"hhhbegins a new JSON structure but is incomplete, which doesn’t cause issues as the command has already been executed
In technical terms, this is a classic example of command injection where user-controlled input (the Telegram message) is directly interpolated into a command string without proper escaping or parameterization.
Coordinates Leak
The Telegram auth plugin had a critical design flaw where it failed to hide a player’s coordinates when they were in an unauthenticated state. This vulnerability allowed anyone to:
- Log in using any player’s username
- View their exact logout coordinates before being kicked for failing authentication
- Use this information to locate hidden bases and secret facilities
This exploit effectively eliminated the concept of “hidden” bases on SarCraft, as determined players could discover anyone’s location by briefly impersonating them at login.
Identity Theft
The most sophisticated and feared exploit in SarCraft history, the “Identity Theft” bug was a fundamental flaw in how the authentication plugin handled player sessions. When multiple players attempted to log in simultaneously, the plugin would become confused about player identities, leading to spectacularly chaotic results:
- Player A and Player B would log in at the same time
- Player A would be thrown into Spectator mode once Player B authenticated
- Player A could now freely fly around without any restrictions
- Player B would be teleported to Player A’s location
- When Player C logged in, Player B would be teleported to Player C’s location
This cascade of teleportations and spectator mode assignments created opportunities for strategic exploitation. WhoIsFishie mastered the timing required to trigger this bug reliably, using it in Season 6 to expose iBattus’s secret End portal room and in Season 8 to teleport iBattus directly to the Warden in what would lead to the infamous “Fish Bundy Trial.”
The root cause lay in the plugin’s design as a wrapper around the Minecraft server which monitored server logs to handle authentication. When multiple player events occurred in rapid succession, the log parser would misattribute actions, creating the identity confusion.
Technical explanation for the bug
Session Exploit
A timing vulnerability in the auth plugin where if a player reconnected immediately after disconnecting, the system wouldn’t request a password verification. The critical flaw was that the plugin didn’t confirm whether the new connection shared the same IP as the session creator.
This exploit became central to one of the most contentious disputes in server history when iBattus accused WhoIsFishie of using it to kill Ssahan in Season 9 - an accusation WhoIsFishie vehemently denied.
Game Mechanics Exploits
Invincibility Glitch
A state bug in the early auth plugin would occasionally place players in limbo between authenticated and unauthenticated states. While in this glitch state:
- Players could deal damage but not receive any
- Movement was restricted, but damage output was unlimited
- Players could effectively become invulnerable turrets
The Nazi faction allegedly exploited this bug during the Ender Dragon fight in early seasons, allowing them to defeat the dragon with minimal gear and preparation.